How Docker improves the security of on-premises solutions
Easy Software is pleased to announce official support of on-premises solution via Docker solutions. This article focuses on the security benefits. I strongly believe you will find them worth the smaller effort of migrating from the legacy solution.
Table of contents
Enhancing on-premises security with Docker
1. Isolation of applications
2. Immutable infrastructure
3. Proactive vulnerability management
4. Controlled access and permissions
5. Network security
6. Image signing and encryption
Docker and Easy Redmine's ISO certification
Strengthening on-premises data protection
Enhancing on-premises security with Docker
Docker enhances the security of on-premises solutions through several key mechanisms that focus on isolation, control, and proactive management of vulnerabilities. Here are the primary ways Docker improves security:
1. Isolation of applications
Docker containers encapsulate applications and their dependencies in isolated environments. This means that each container runs as a separate process, which limits the potential damage that can be caused by a breach. If a malicious actor gains access to one container (e.g. application), they cannot easily affect others (e.g. database) or the host system, thus reducing the overall attack surface.
2. Immutable infrastructure
The use of immutable infrastructure is promoted by Docker, where containers are replaced with fresh versions rather than being patched in place. This approach minimizes configuration drift and reduces vulnerabilities associated with outdated software. By deploying new containers with updated code and dependencies, organizations can ensure that their applications are running the latest and most secure versions.
In the context of Easy Redmine, no need to manually upgrade Ruby, DB server and others, all is done by replacing the old images with the new ones with the use of docker compose. Making the update process easier motivates more regular updates.
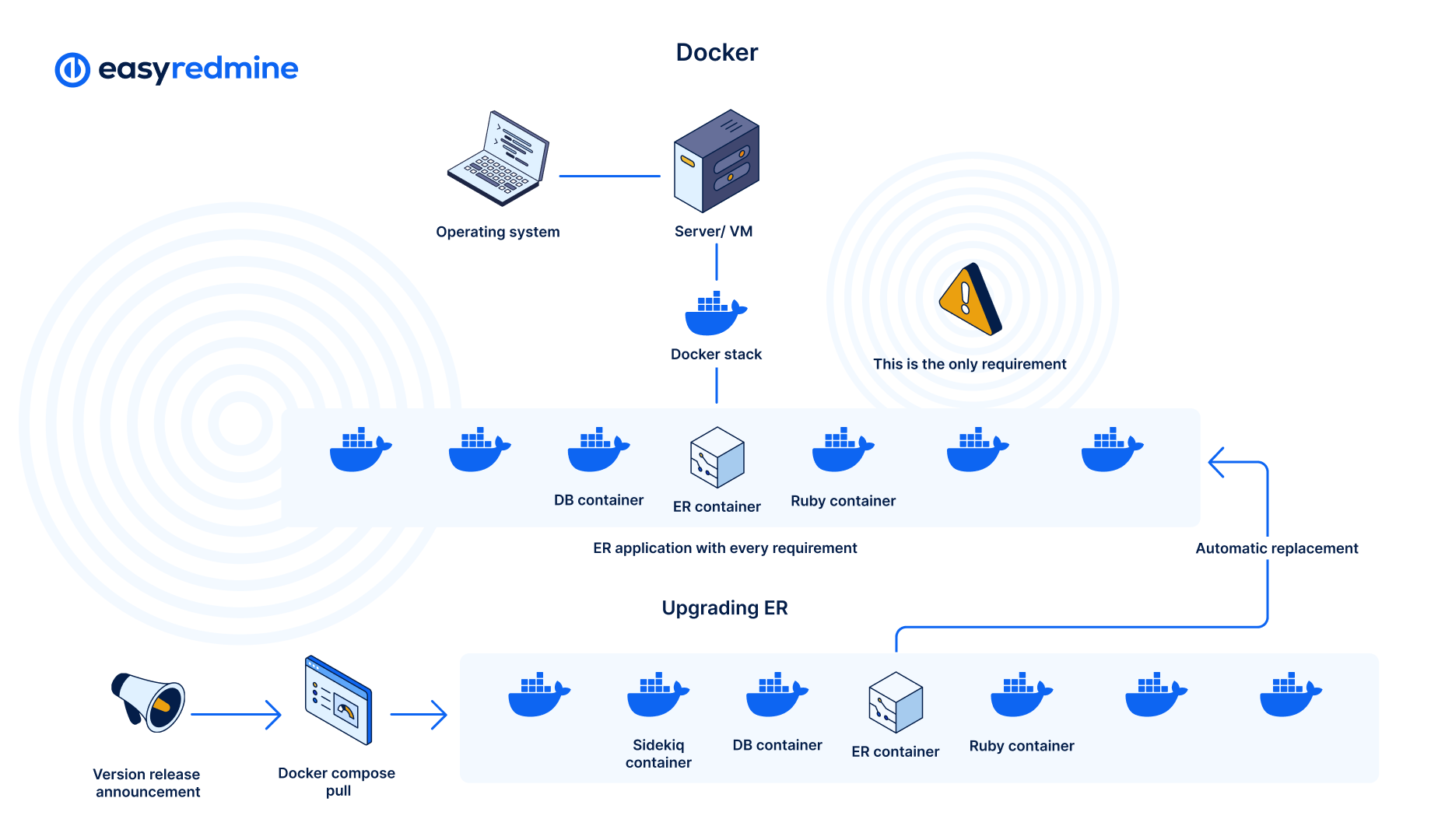
Docker schema by Easy Redmine
3. Proactive vulnerability management
Docker provides tools for scanning images for vulnerabilities before they are deployed. For example, Docker Scout allows users to analyze container images for known security issues and suggests remediation steps. Regularly scanning images helps identify and address vulnerabilities early in the development cycle, preventing them from reaching production environments.
While Easy Software guarantees the contents of provided images, you may add a layer of control, if your company policies require.
4. Controlled access and permissions
Docker supports role-based access control (RBAC), which allows organizations to define permissions for users and applications. By enforcing strict access controls, organizations can limit who can deploy or modify containers, thereby reducing the risk of insider threats or unauthorized changes to critical applications.
5. Network security
Network segmentation between containers is enabled by Docker, helping to prevent unauthorized access and data leaks. It allows to control ingress and egress traffic with network security policies, organizations can secure communication channels between containers and external services, further protecting sensitive data from potential attacks.
6. Image signing and encryption
To ensure the integrity of container images, Docker supports image signing and encryption practices. This ensures that only verified images are deployed in production environments, mitigating risks associated with tampering or unauthorized modifications.
Docker and Easy Redmine's ISO certification
Easy Redmine and Docker are increasingly recognized for their roles in enhancing security within project management and application deployment. Both technologies offer distinct advantages that help organizations manage security more effectively.
Our AI-powered software is certified with ISO 27001, 27017, and 9001, which underscores its commitment to maintaining high standards in information security and quality management. Docker also received a SOC 2 Type 2 attestation, which evaluates the effectiveness of internal controls over security, availability, confidentiality, processing integrity, and privacy.

Strengthening on-premises data protection
By leveraging mentioned security features, Docker not only enhances the safety of on-premises solutions but also provides a robust framework for managing security risks associated with modern application deployment. The combination of isolation, proactive vulnerability management, controlled access, and secure networking makes Docker a valuable tool for organizations seeking to improve their security posture in an increasingly complex threat landscape.
To verify these statements yourself with Easy Redmine, visit the Client Zone to find the instructions to deploy your Docker image. Prepare a test environment and follow the instructions. We are confident the benefits will become obvious.
Not having your Client Zone yet? Try Easy Redmine, adaptive project management software that can be (apart from the cloud) deployed on your server! New version 14 is powered by Easy AI that can be deployed on-premises for the max data protection.